Cloudera: Specifying LDAP Settings
Arcadia Enterprise enables you to specify LDAP sign-in authentication settings in Cloudera Manager.
For general information about user authentication, see Configuring User Authentication Using LDAP.
After Installing Arcadia Enterprise Using Cloudera Manager, perform the following steps on the Cloudera Manager interface to specify LDAP settings:
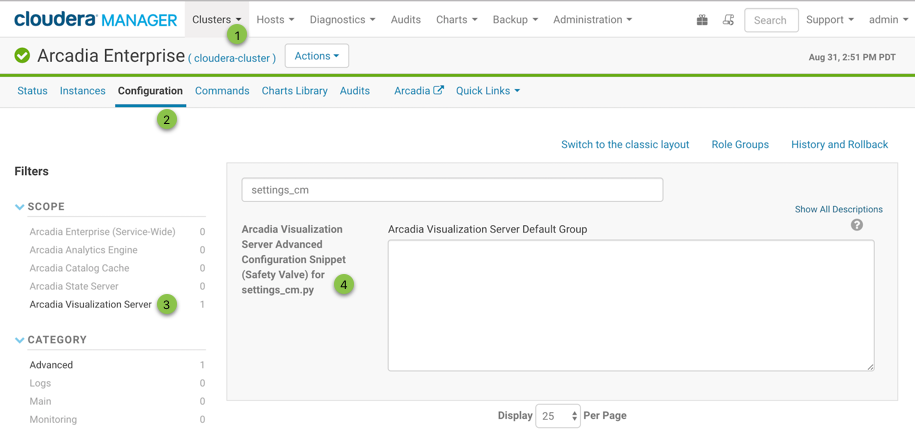
- Log into Cloudera Manager and click Clusters in the top navigation menu.
- Under Arcadia Enterprise, click Configuration in the top menu bar.
- On the Configuration page, under Filters > Scope, click Arcadia Visualization Server.
- Search for the Arcadia Visualization Server Advanced Configuration
Snippet (Safety Valve) for settings_cm.py field.
Display Field for Entering LDAP Settings - In the Safety Valve field, use the following
sample code for Active Directory, and modify the settings as
appropriate. For more information, see https://django-auth-ldap.readthedocs.io/en/latest/reference.html.
import ldap from django_auth_ldap.config import LDAPSearch, NestedActiveDirectoryGroupType # Connection options # AUTH_LDAP_START_TLS = True AUTH_LDAP_SERVER_URI = "ldap://host:port" # Bind user AUTH_LDAP_BIND_DN = "CN=arcadmin,CN=Users,DC=arctest,DC=arcadiadata,DC=com" AUTH_LDAP_BIND_PASSWORD = "Password" # Required Group for all users AUTH_LDAP_REQUIRE_GROUP = "CN=arcviz users,CN=Users,DC=arctest,DC=arcadiadata,DC=com" # Group for Admins (Optional) AUTH_LDAP_USER_FLAGS_BY_GROUP = { "is_superuser": ["CN=arcviz admins,CN=Users,DC=arctest,DC=arcadiadata,DC=com"] } # User and group search objects and types AUTH_LDAP_USER_SEARCH = LDAPSearch("CN=Users,DC=arctest,DC=arcadiadata,DC=com", ldap.SCOPE_SUBTREE,"(sAMAccountName=%(user)s)") AUTH_LDAP_GROUP_SEARCH = LDAPSearch("CN=Users,DC=arctest,DC=arcadiadata,DC=com", ldap.SCOPE_SUBTREE, "(objectClass=group)") # Map LDAP attributes to Django AUTH_LDAP_USER_ATTR_MAP = { "first_name": "givenName", "last_name": "sn", "email": "mail" } # Cache settings # Note this may cause a delay when groups are changed in LDAP AUTH_LDAP_CACHE_GROUPS = True AUTH_LDAP_GROUP_CACHE_TIMEOUT = 300 # Group Settings AUTH_LDAP_GROUP_TYPE = NestedActiveDirectoryGroupType() AUTH_LDAP_FIND_GROUP_PERMS = True AUTH_LDAP_MIRROR_GROUPS = False # Some optional TLS/SSL options # AUTH_LDAP_GLOBAL_OPTIONS = { # ldap.OPT_X_TLS_CACERTFILE: "/etc/bla.cert", # Point to CA Cert file # ldap.OPT_X_TLS_REQUIRE_CERT: ldap.OPT_X_TLS_NEVER, # Disable cert checking # } AUTH_LDAP_CONNECTION_OPTIONS = { ldap.OPT_DEBUG_LEVEL: 1, # 0 to 255 ldap.OPT_REFERRALS: 0, # For Active Directory } # If there is no Bind User you can use these settings, but it's not the preferred way # AUTH_LDAP_BIND_AS_AUTHENTICATING_USER = True # AUTH_LDAP_USER_DN_TEMPLATE = "CN=%(user)s,CN=Users,DC=arctest,DC=arcadiadata,DC=com" # The backend needed to make this work. AUTHENTICATION_BACKENDS = ( 'django_auth_ldap.backend.LDAPBackend', 'django.contrib.auth.backends.ModelBackend' ) - Click Save Changes to save the configuration.
-
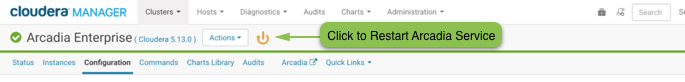
To restart Arcadia Enterprise service and apply configuration changes, click the orange icon in the Arcadia Enterprise menu bar.
Restarting Arcadia Enterprise Service -
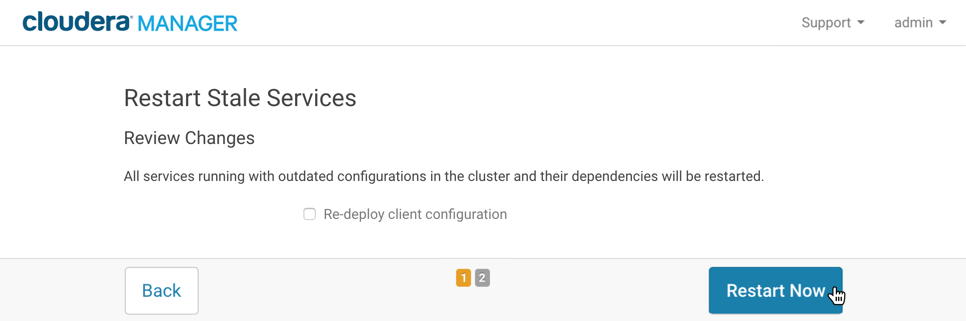
In the Restart Stale Services interface, click Restart Now to restart Arcadia Enterprise service.
Confirming Restart of Arcadia Enterprise Service
After Arcadia Enterprise service successfully restarts, LDAP is set up successfully.